- What is volatility forensic tool?
- For what purpose volatility tool is used?
- What is volatility framework?
- Does Kali have volatility?
- How is volatility used in trading?
- What is volatility cyber security?
- What type of data is the most volatile?
- What is memory analysis?
- Can be used to determine hidden and terminated processes in volatility tool?
- What is volatile RAM?
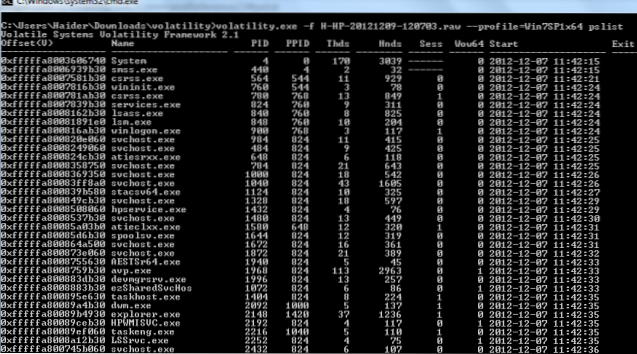
- How do I run volatility in Windows?
- Which Kali Linux tool allows the examination of a memory dump file?
What is volatility forensic tool?
Volatility is an open-source memory forensics framework for incident response and malware analysis. It is written in Python and supports Microsoft Windows, Mac OS X, and Linux (as of version 2.5).
For what purpose volatility tool is used?
Volatility is one of the best open source software programs for analyzing RAM in 32 bit/64 bit systems. It supports analysis for Linux, Windows, Mac, and Android systems. It is based on Python and can be run on Windows, Linux, and Mac systems. It can analyze raw dumps, crash dumps, VMware dumps (.
What is volatility framework?
The Volatility Framework is a completely open collection of tools, implemented in Python under the GNU General Public License, for the extraction of digital artifacts from volatile memory (RAM) samples.
Does Kali have volatility?
To start the Volatility Framework, click on the All Applications button at the bottom of the sidebar and type volatility in the search bar: Clicking on the volatility icon starts the program in a Terminal.
How is volatility used in trading?
Trade Volatility with Options
When using options to trade volatility, a trader could buy a call option and a put option with the same strike price and expiration date. If the underlying instrument experiences a large price-move, either the put or call option will become in-the-money and return a profit.
What is volatility cyber security?
Volatility is an open source memory forensics framework for incident response and malware analysis. Volatility is the world's most widely used memory forensics platform. ... Volatility also provides a unique platform that enables cutting edge research to be immediately transitioned into the hands of digital investigators.
What type of data is the most volatile?
Data in memory is the most volatile. This includes data in central processor unit (CPU) registers, caches, and system random access memory (RAM). The data in cache and CPU registers is the most volatile, mostly because the storage space is so small.
What is memory analysis?
Memory forensics (sometimes referred to as memory analysis) refers to the analysis of volatile data in a computer's memory dump. Information security professionals conduct memory forensics to investigate and identify attacks or malicious behaviors that do not leave easily detectable tracks on hard drive data.
Can be used to determine hidden and terminated processes in volatility tool?
To enumerate processes using pool tag scanning ( _POOL_HEADER ), use the psscan command. This can find processes that previously terminated (inactive) and processes that have been hidden or unlinked by a rootkit.
What is volatile RAM?
Volatile memory, in contrast to non-volatile memory, is computer memory that requires power to maintain the stored information; it retains its contents while powered on but when the power is interrupted, the stored data is quickly lost. ... Most of the general-purpose random-access memory (RAM) is volatile.
How do I run volatility in Windows?
Installation
- Download and install Python 2.7. ( The Volatility setup script doesn't currently support Python 3). ...
- Download the Volatility source code archive and extract files.
- Open a command prompt, navigate to the location you extracted the Volatility source to and run “setup.py install”
Which Kali Linux tool allows the examination of a memory dump file?
The Volatility Framework is a completely open collection of tools, implemented in Python under the GNU General Public License, for the extraction of digital artifacts from volatile memory (RAM) samples.
 Linuxteaching
Linuxteaching